How to store sensitive info?
What is sensitive info?
- Token storage, secrets
- Certificates, tokens, passwords
Can I save sensitive info in codes?
- Never store sensitive API keys in your app code
- Anything included in your code could be accessed in plain text by anyone inspecting the app bundle
Can I use react-native-dotenv, react-native-config or AsyncStorage to store sensitive info?
- No. They are good for saving API endpoints only
- Async Storage is the React Native equivalent of Local Storage from the web
What libraries can I use to save my sensitive info?
You can save it to iOS keychain services or Android Secure Shared Preference
You can use react-native-keychain
Can we add extra layer before saving sensitive info?
Yes. Encrypt values before saving them
How to secure network communication?
How to avoid man-in-the-middle-attack?
- Always use https for API request
- SSL encryption protects against the requested data being read in plain text between when it leaves the server and before it reaches the client.
- Using https endpoints could still leave your data vulnerable to interception.
- Use SSL pinning to avoid man-in-the-middle-attack
- App security is depending on Certificate Authorities (CA) and Domain Name Servers (DNS) to validate domain’s TLS (Transport Layer Security).
- But SSL pinning can be used to migrate the risk of installing the unsafe certificates on the user devices.
- Commonly we use “FETCH” API or libraries like “AXIOS” or “FRISBEE” to consume APIs in React Native apps, but these APIs and Libraries do not support SSL pinning.
- Should be mindful of certificate expiry when using SSL pinning.
Certificates expire every 1–2 years and when one does, it’ll need to be updated in the app as well as on the server.
As soon as the certificate on the server has been updated, any apps with the old certificate embedded in them will cease to work.
How to know authentication and token exchange requests come from the same client?
To be more secure with OAuth-2 as an extension we can use SHA 256 cryptographic algorithm which ensures that the authentication and token exchange requests come from the same client.
SHA 256 creates a unique “signature” for a text or file. The signature is always the same length and for same inputs signature will always be same. This whole process is known as Proof of Key Code Exchange(PKCE).
How to encrypt Javascript codes, native Android/ iOS codes?
Obfuscate the codes to avoid reverse engineering with APK/ ipa or app bundle file.
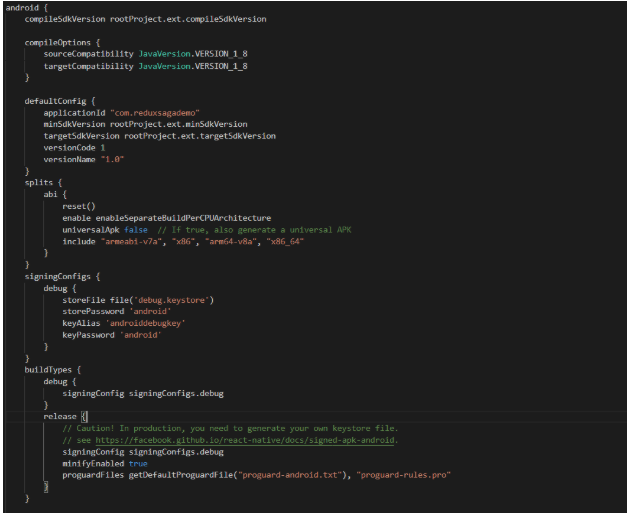
Android
Add Pro Guard rule by enabling the minifyEnabled property in app/build.gradle file.
iOS
- Restrict insecure domains by configuring some policies within Info.plist file
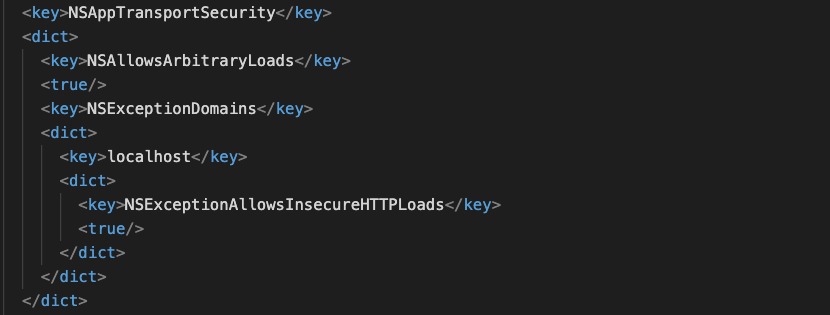
- NSAllowArbitraryLoads which is set to NO (default) means you have agreed with security benefits.
- Make it YES when working with localhost or with HTTP domain
- App will get rejected because you set NSAllowArbitraryLoads value as YES.
To overcome that you can use NSExceptionDomains.- App will consider like you have agreed to all over security benefits excepts the domain those domains which you have mentioned in NSExceptionDomains (although you have set NSAllowArbitraryLoads value as YES).
How to detect unprotected devices?
- Use Runtime Application Self-Protection service.
- It wraps whole application with their own code, which detects any malicious software that can be present in users device and either blocks all unwanted interactions (like reading users input with screen readers), or shutting down the app completely if the threat is severe and there’s a risk of user’s data being compromised.
- How to detect Android rooted devices, bootloader unlocks, bad URLs, device tampering, potentially harmful apps and fake users?
- How to identify jail-broken or rooted for iOS/Android; detect if mock locations can be set using “Developer Mode”?
- Use JailMonkey https://github.com/GantMan/jail-monkey#readme
References
https://reactnative.dev/docs/security
secure-your-react-native-app
building-a-secure-mobile-app-with-react-native
security-aspects-to-consider-for-a-react-native-application
Leave a Reply